In order to ensure that customers have highly information security of internet datacenter and networks, and also to ensure that the security of important data and systems after the cloud meets international standards, Chief has invested huge resources in recent years and has obtained ISO 27001, ISO 27011, ISO 27017 and ISO 27018. The international quadruple security certification ensures the security of the information in the Chief IDC and the network, and ensures the security of important data and system in the cloud.
Chief APP Cloud provides a complete security solution for customers from the end to the cloud, whether it is to enhance the user’s secure login, or to provide anti-virus and anti-malware for the server farm, and provide related defense services such as IPS and WAF. Customers can feel at ease to use Chief cloud service.
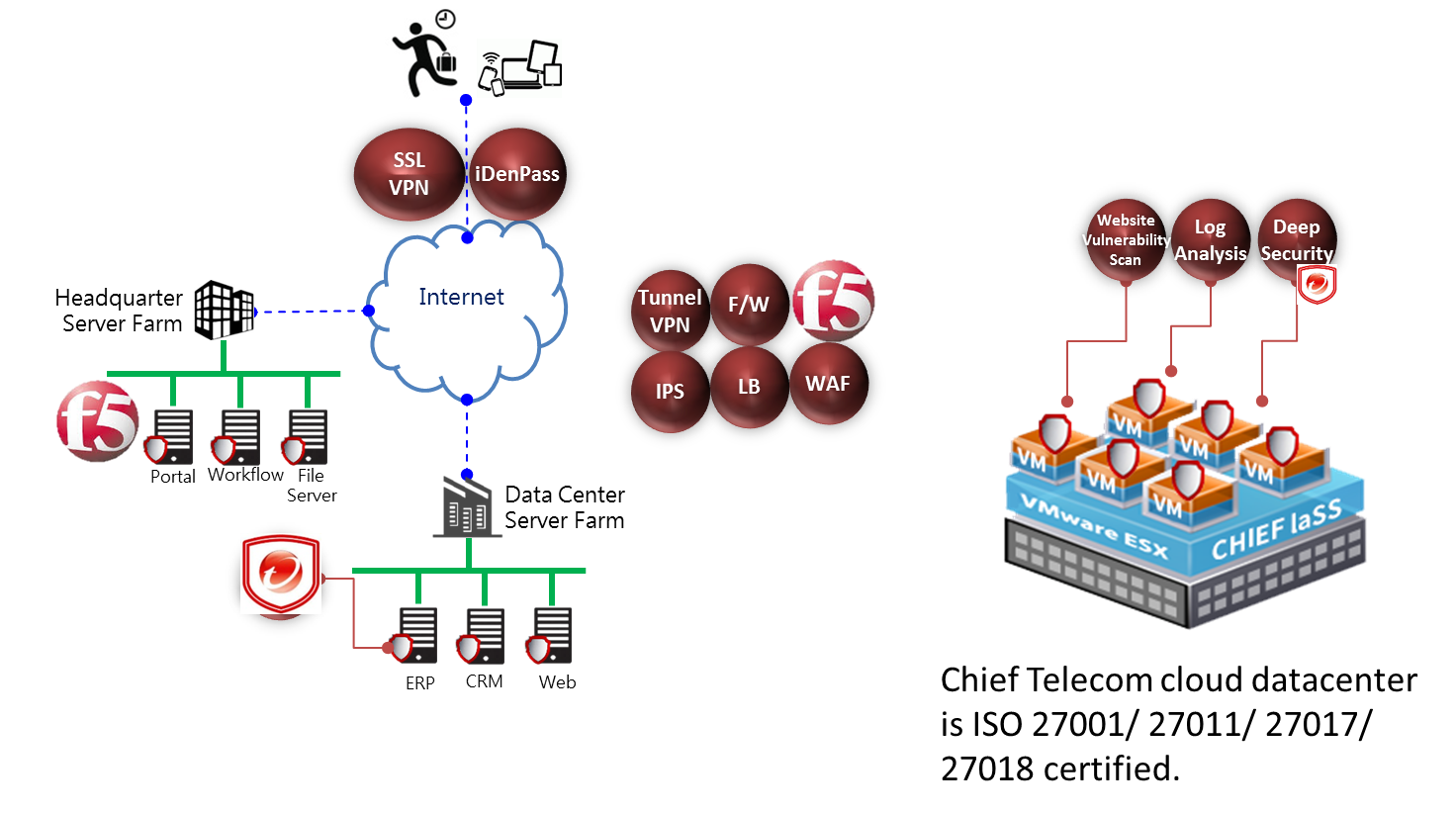
Information Security Applications

F5 Cloud-Based Information Security Application Solution
Chief cloud-based information security application solution deploys its infrastructure in Chief Cloud IDC and combines cloud-based F5 applications to provide enterprise customers with a cloud solution that is easy to deploy and complies with enterprise information security guidelines. Enterprise users are able to enjoy international grade of information security services provided by F5 applications with only monthly rental, and use applications such as load-balancing, firewall, WAF, anti-DDoS and mobile secure access. Chief also provides license rental of software-version F5 applications so that it can fulfill customer’s overall information security requirement in a hybrid cloud structure.

Cloud VM Information Security Protection
Chief cloud computing platform service not only takes care of the security of physical and network infrastructure levels and hypervisor, but also strengthens cloud VM’s information security and verification mechanisms, so as to protect customers’ OS, applications and data on the cloud. Deep Security Service provides speedy deployment process and eliminates information security breaches, protecting system workload as well as maintaining flexibility.
The service supports public clouds, hybrid clouds and multi clouds, and safeguards all platforms. Through the installation of Agents, enterprises can monitor and protect their server farm no matter it is located inside the HQ, datacenters, or even the VM on Chief Telecom IaaS platform.

Professional Information Security Solution
Chief Telecom’s team of information security experts assist customers on customizing the required information security solutions, ranging from endpoint protection, and all sorts of software and hardware integration.
Chief Telecom can also provide cloud computing security and vulnerability management, cloud service efficacy assessment and third-party verification to provide enterprise customers and Chief AppCloud providers with tools to examine the security and compliance degree of their applications. Therefore, information security risks are either prevented or mitigated.

Log Analysis
Enterprise users will not need to spend a lot of funds on software/hardware for log collection and storage every year now. With LogAnalysis, enterprise users can upload system logs, network equipment logs, information security incident logs and NetFlow/sFlow data to LogAnalysis through internet, and complete the task of log storage and management. A dedicated Portal will be available for enterprise users to check daily logs and produce necessary statistics reports.

